Threesome app exposes 1.5 million users' data from White House to 10 Downing Street
3Fun has been categorized as being probably the worst security for any dating app ever seen.â€

Dating apps are a dime and dozen these days and while the vanilla ones like Tinder and Bumble get the maximum exposure because of its well-deserved success rates; there are speciality ones that cater to various kinks and fetishes. One such app is 3Fun which is extremely popular with the swinger and threesome community that’s described as “Curious Couples & Singles Dating" and it's for individuals 18 years and older unsurprisingly. However, what’s alarming is that its security measures are not in place and security researchers have described it as a “privacy train wreck.”
The swingers platform has over 100,000 active installs on Android alone with 3Fun claiming that it has an audience of over 1.5 million users world over. While the devs of the app claim to have its privacy protections in place, with implementations such as private photo albums, certain researchers from Pen Test claim that 3Fun’s claims are farthest from the truth.
As per tester Alex Lomas, 3Fun has earned the dubious award of being “probably the worst security for any dating app we’ve ever seen.”
As per a related report by ZDNet, this “privacy trainwreck” did not only expose the real-time location of its users, whether home, work or during their daily commute, but also leaked dates of its user’s birth, sexual preference, chat information as well as private pictures even though users enabled additional privacy systems for the latter.
Because of ‘trilateration’ user data leaks in similar mobile dating apps like Grindr and Romeo have also appeared recently. This trilateration is a method used to spoof GPS coordinates and exploit “distance from me” features in an app to zone in on a user’s location.
The Pen Test researchers state that 3Fun’s security measures are nowhere nearly as sophisticated as Grindr or Romeo as the app leaks your information outright. The latitude and longitude of a user in close to real-time were easily available and there was no need to make calculations based on rough coordinates. The researchers state that while users can restrict location exposure through settings is only filtered on the app itself which is sent to 3Fun’s servers through a GET request.
The researchers stated, “It's just hidden in the mobile app interface if the privacy flag is set. The filtering is client-side, so the API can still be queried for the position data."
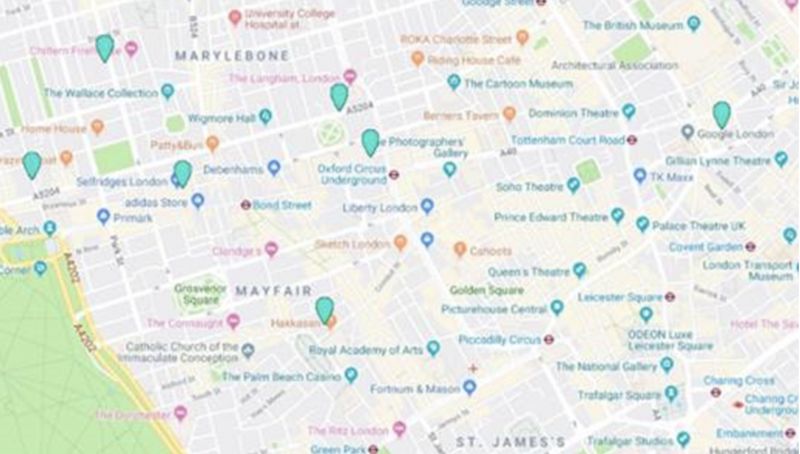
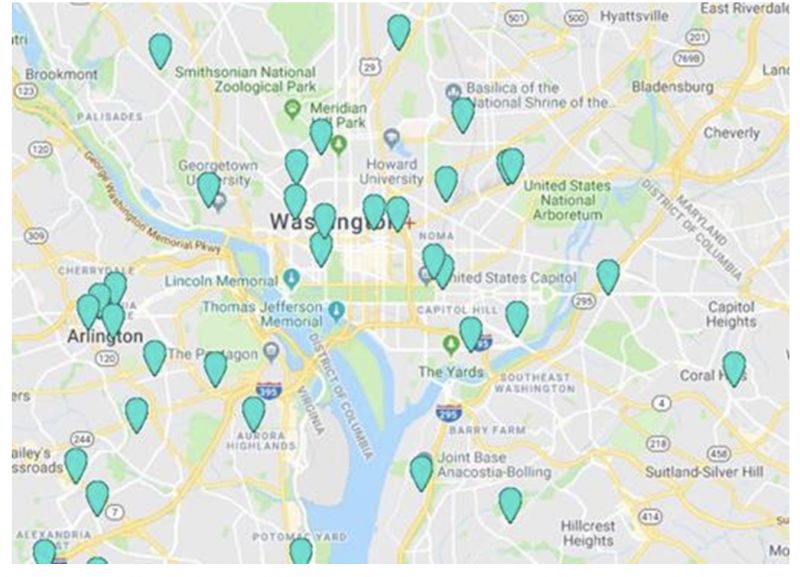
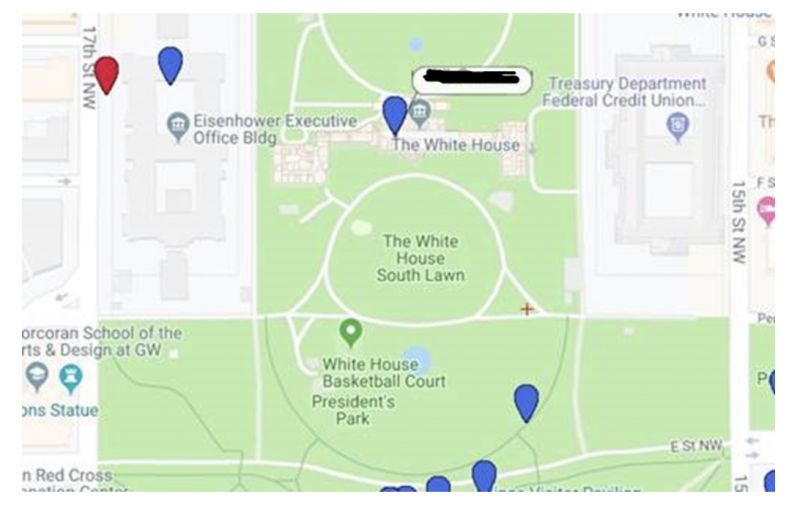
As per ZDNet, “the exact location of users was accessible by querying the API. Location maps viewed by the team ranged from London as a whole to the home of the prime minister, Number 10, Downing Street, as well as Washington DC, the US Supreme Court, and the White House. “
While you can spoof GPS coordinates to have a laugh with location tracking, this doesn’t detract from the severity of the overall data leak. Combining this information with the users’ date of birth, it can be possible to stalk and unmask the individuals. Apart from this, private pictures were also available for all to see as the URLs of the images that are hidden and meant to be private were exposed during API activity.
The researchers believe that there could be more vulnerabilities that can be found in its mobile app and its API but were not able to further investigate.
This finding was disclosed on July 1, 2019, and they informed 3Fun about it. However, the response they received from the developers leaves a lot to be desired. 3Fun states, “Dear Alex, Thanks for your kindly reminding. We will fix the problems as soon as possible. Do you have any suggestion? Regards, The 3Fun Team."
