Google arms Pixel 2 against hackers, with a secret chip
Since the dedicated chip is responsible only for this function, it will be tough for the hackers to use software-based bruteforce attack.

Security is one area of smartphones that people some people highly value, and there is a good reason for that. After all, you interact with your phone more than any other gadget. An average user captures and stores most of his photos and videos on the phone, keeps his emails and social accounts logged in and synced. What if someone bypasses your passcode and gains access to this data?
Android as a platform is open source and despite its versatility, it is known to have more security vulnerability than competing systems such as the closed source iOS.
Now Google realised this and fitted special hardware feature in their Pixel 2 and Pixel 2 XL devices.
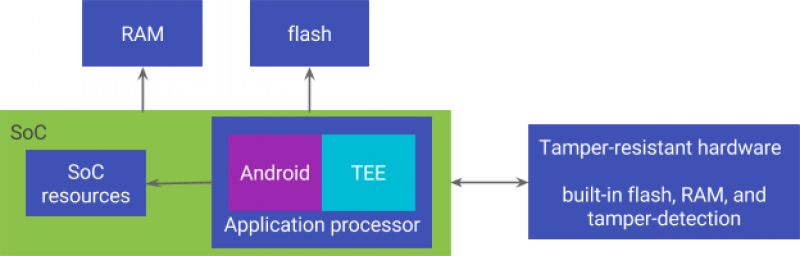
In a blog post, they have detailed that the new Google Pixel 2 devices ships with a dedicated hardware security module designed to resist physical attacks. This hardware module performs lockscreen passcode verification and protects the lock screen better than software alone.
 Pixel 2 has a dedicated hardware solution against hacking
Pixel 2 has a dedicated hardware solution against hacking
Since Android 7.0 Nougat, the act of getting by your lock screen has been verified in a secure environment. Android uses your lock-screen passcode to derive the key that is then used to encrypt your data. In case you unlock your phone for the first time after a reboot, an attacker cannot recover the key (and hence your data) without knowing your passcode first. This is to limit how many times they can brute-force guess their way into your phone when locked.
Google has armed this secure environment with a dedicated hardware that comes in form of a tamper-resistant chip separate from the system on a chip (SoC) and includes its own flash, RAM, processing unit, and other resources.
Now the passcode verification takes place in this secured hardware module instead of the software. Since the dedicated chip is responsible only for this function, it will be difficult for the hackers to employ software-based brute force techniques.
Google further details even in the event of a full compromise elsewhere, the attacker cannot derive your disk encryption key without compromising the security module first. The chip is further designed to withstand various physical fault injection, physical penetration and side channeling techniques used by hackers to compromise your data.
