Adware found in lifestyle apps on the Google Play Store: Avast
The apps are surprisingly seen with over 20 million installs.

Avast, a global leader in digital security products, announced that it discovered 40 adware apps on the Google Play Store using Avast’s mobile threat intelligence platform, apklab.io. The installations of the apps, which Avast is referring to as TsSdk, range from 5K to 5M installations. The adware persistently displays full screen ads, and in some cases, tries to convince the user to install further apps.
The adware applications are linked together by the use of third-party Android libraries which bypass the background service restrictions present in newer Android versions. Although the bypassing itself is not explicitly forbidden on the Play Store, Avast detects it as Android:Agent-SEB [PUP], because apps using these libraries waste the user’s battery and make the device slower. The applications use the libraries to continuously display more and more ads to the user, going against Play Store rules.
Avast has contacted Google to have the apps removed. Avast named the adware TsSdk, because the term was found in the first version of the adware.
The original
Using apklab.io, Avast found two versions of TsSdk on the Play Store all linked together by the same code. The older of the two versions has been installed 3.2 million times and was contained in simple gaming, fitness, and photo editing applications; most often installed in India, Indonesia, Philippines, Pakistan, Bangladesh and Nepal.

Above, an example of one of the apps containing TsSDK.
Once installed, most of the apps containing the older version appear to work as advertised on their Google Play pages, however, additionally, shortcuts are dropped onto the home screen and full screen ads are shown to the user when they turn the screen on, and in some cases, the ads are shown periodically when the user uses the device. In some cases, the apps contain code capable of downloading further applications, prompting the users to install them. Additionally, most of the older samples also added a shortcut to a “Game Center” on the infected device’s home screen, which opens a page advertising different games: http://h5games.top/.

The name “H5GameCenter” was also part of the Cosiloon preinstalled malware Avast reported on last year. The Avast researchers are unsure if the two are related to one another.
Updating the adware code
The newer version has been installed 21 million times and was included in music and fitness apps. The targets where the apps are most installed are in India, Phillipines, Indonesia, Malaysia, Brazil, and the UK. The new version’s code is better protected; the code is encrypted using the Tencent packer, which is rather hard to unpack by analysts, but is easily captured during dynamic analysis in apklab.io.
This version carries out several checks before deploying full-screen ads. First and foremost, the adware is only triggered if the user installs the app by clicking on a Facebook ad. The application can detect this using a Facebook SDK feature called “deferred deep linking”.
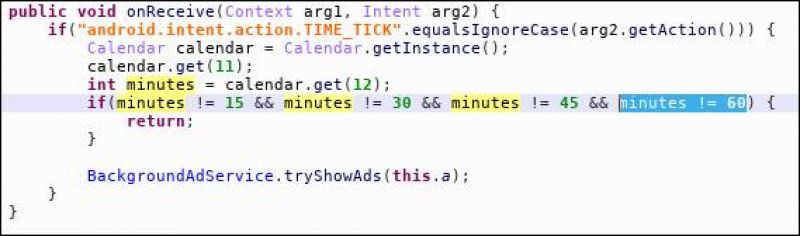
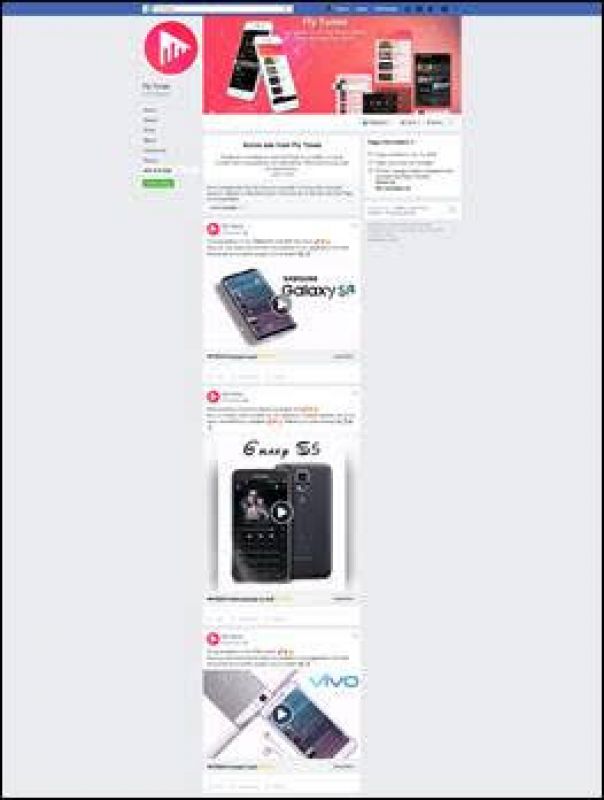
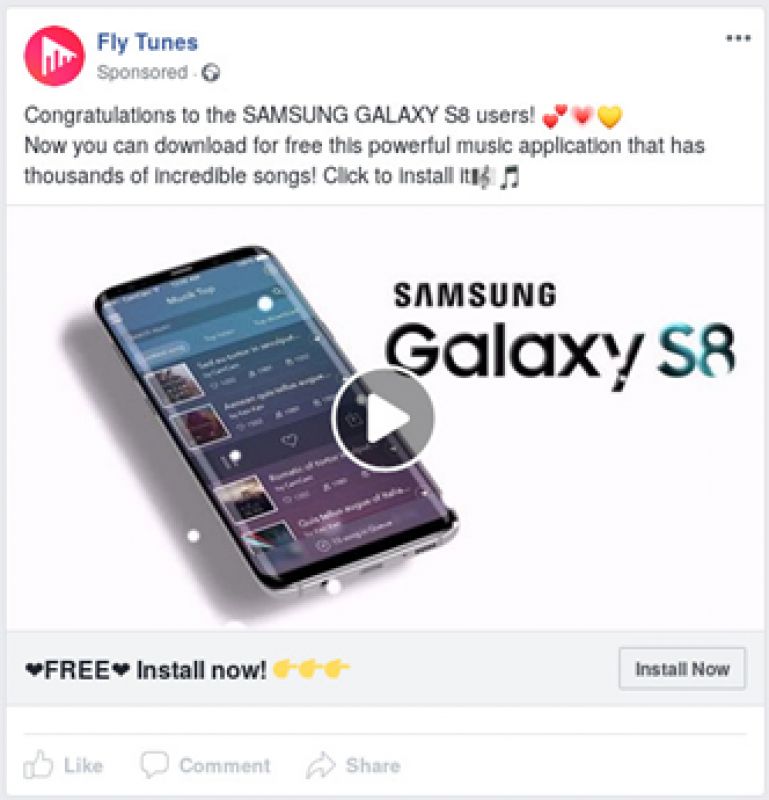
The adware only shows ads within the first four hours of the app being installed and then much less frequently. From the code, we know that within the first four hours, full screen ads are displayed randomly when the phone is unlocked or every 15 minutes, at 15 minutes, 30 minutes after the hour.
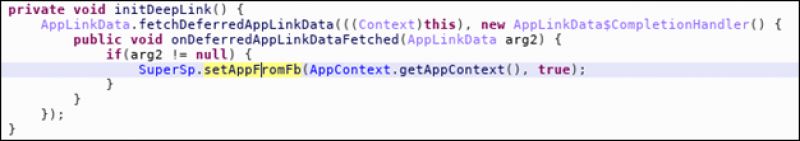
The newer version of the adware doesn’t seem to work on Android version 8.0 and above because of changes in the background service management in these newer Android releases. Due to the amount of samples, Avast only selected the latest APK from each app and put them into this spreadsheet.
Screenshots from Google Play Store and the Facebook pages are available here.
Many of the older version of the adware were on the Play Store before, with Google removing the apps, including an app called Pro Piczoo, which was installed more than one million times.
Tips to avoid adware
Exercise caution when downloading apps. Read app reviews before installing a new app, carefully reading both positive and negative reviews. Notice if reviewers comment on whether or not the app does what it says it will do. If an app’s review includes comments like “this app doesn’t do what it promises” or “this app is packed with adware,” - one should reconsider downloading the app. Reviews like this are a sign that something isn’t right.
Always carefully check app permissions, closely looking to see if they make sense. Granting incorrect permissions can send sensitive data to cybercriminals, including information such as contacts stored on the device, media files and insights into personal chats. If anything seems out of the ordinary or beyond what seems appropriate, the app should not be downloaded.
Install a trustworthy antivirus app. Antivirus acts as a safety net, and can identify apps that are infected with adware, protecting users from these unwanted apps.
